Audit Log Report
Security & Activity Monitoring
The Audit Log Report is a key security feature designed to enhance transparency, accountability, and control within your system. It provides a comprehensive trail of user actions, ensuring that sensitive operations like profile updates, data edits, and manual entries are reviewable at any time.
Why This Matters for Security
By tracking who changes what and when, the audit log acts as a digital paper trail that protects your organization against unauthorized activity, internal misuse, and data integrity issues. It supports:
Access accountability
Data governance and compliance
User training oversight
What You Can Monitor
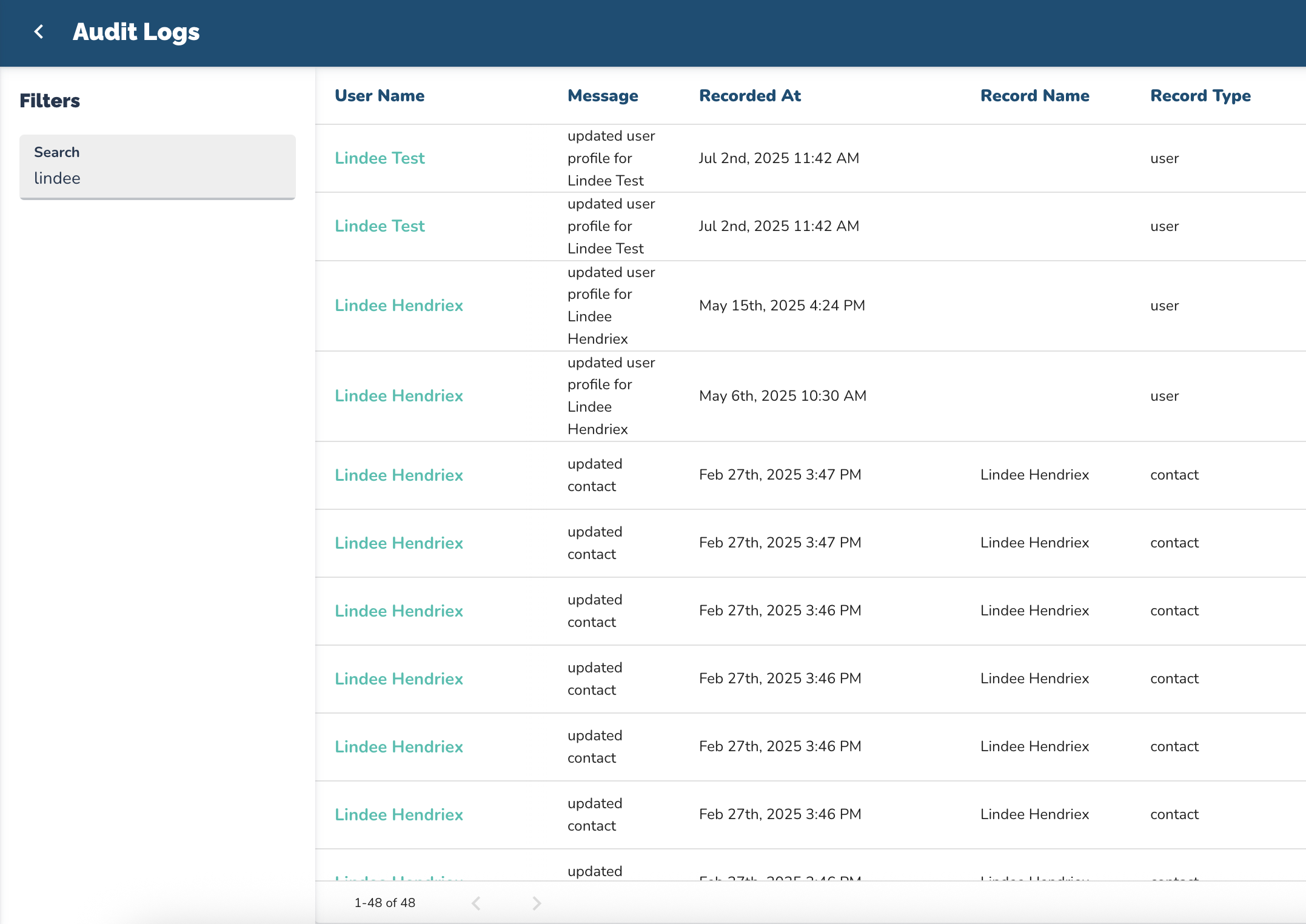
The audit log captures critical user events across your system:
1. Contact Profile Changes
Security Relevance: Prevents unauthorized data tampering or improper contact manipulation.
Details Logged:
User who made the change
Time and date of change
Logs when a contact profile was deleted
2. Contact Creation and Contact Exports
Security Relevance: Detects potential unauthorized or unverified data entries.
Details Logged:
User who created the contact
User who exported contact information
Entry timestamp
User who updated contact profiles
User who updated or deleted a group
3. User Profile Updates
Security Relevance: Protects user identity records and access roles from unauthorized updates.
Details Logged:
Changes to name, email, role, or permissions
User who made the change or deleted the user profile
Timestamps
How to Access the Audit Log
Navigate to Reports.
Select “Audit Log”.
View in-dashboard or export logs securely (CSV format). You can export this report for your records by clicking "Export" at the top right corner of the report.
Permission-Based Access
Audit Logs are only visible to users with the appropriate admin permissions. If you need access and don't see the audit log feature, contact your system administrator.